Application
WhaTap provides the database log monitoring service. You can collect logs from server-installed databases and AWS RDS that is a cloud service. Through this, you can check the scattered logs in the database at a glance in Live Tail and Log Trend for log monitoring.
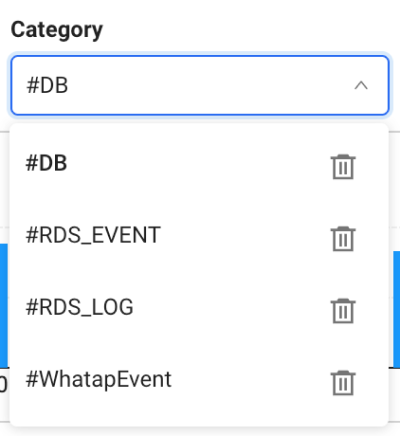
After log monitoring has been applied, installed DB is displayed as #DB, AWS RDS as #RDS_LOG, and #RDS_EVENT in Category of each menu and the log list.
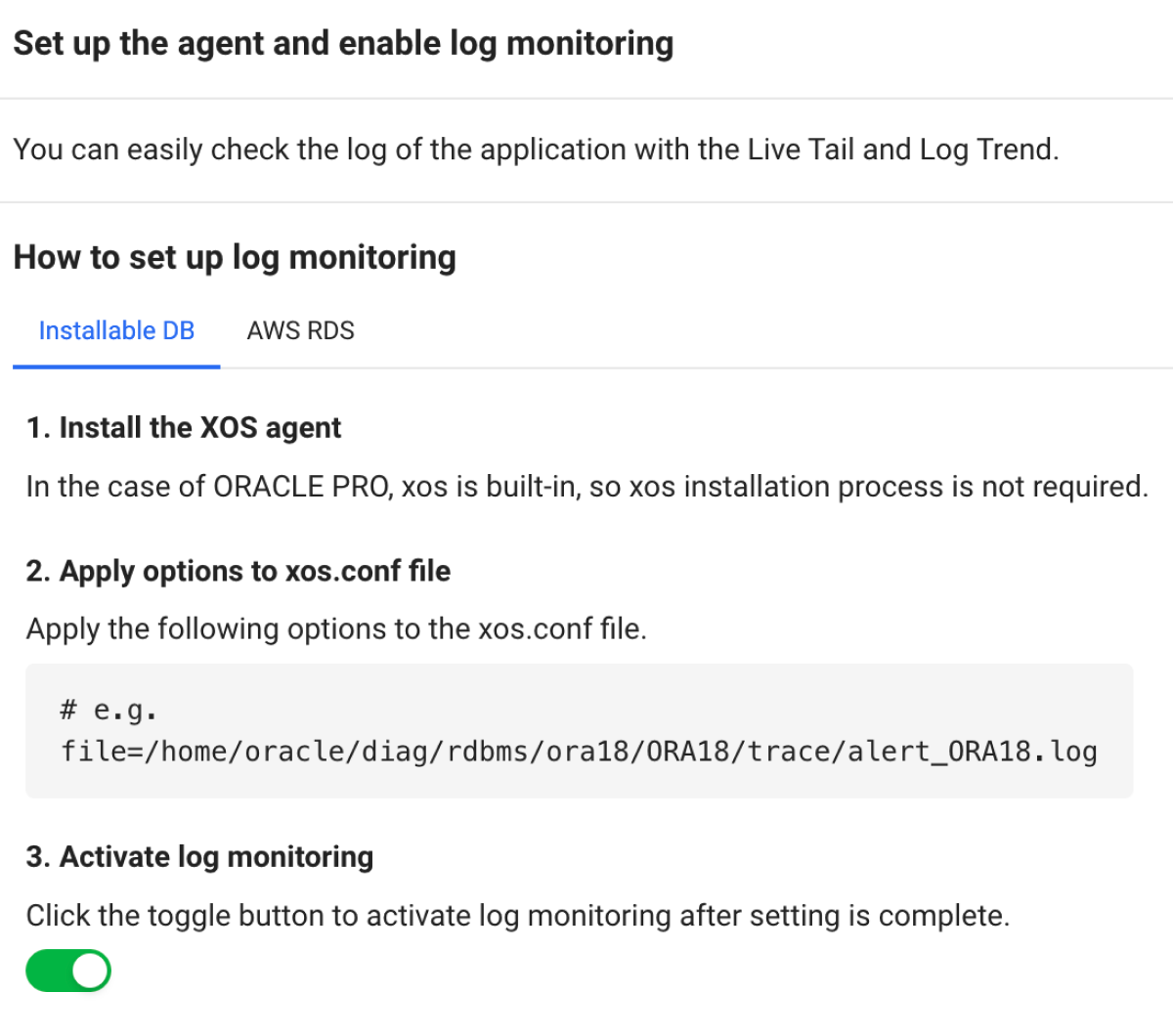
Applying to the server-installed DB
To monitor logs in server-installed databases, apply the following options in xos.conf file.
file=/home/oracle/diag/rdbms/ora18/ORA18/trace/alert_ORA18.log
Oracle Pro products come with the built-in XOS agent, eliminating the need for a separate installation process.
Applying to the AWS RDS logs
Configuration for monitoring AWS RDS logs
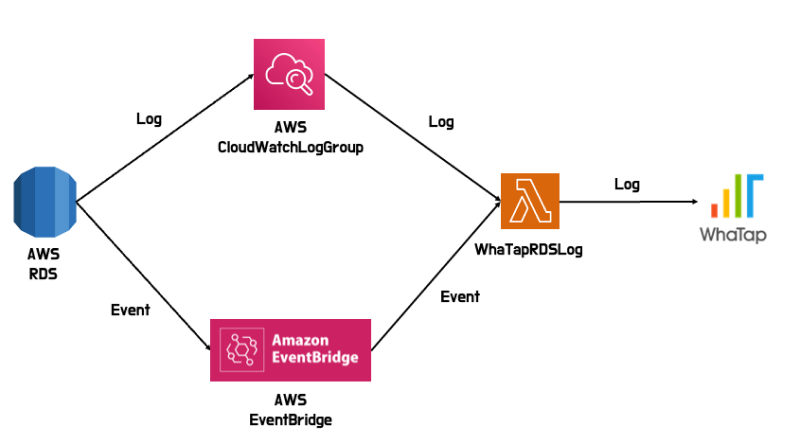
AWS provides various information for RDS monitoring. To check information, directly access the AWS console. However, WhaTap's AWS RDS Log provides logs and events from RDS in Log under Database Monitoring.
WhaTap's AWS RDS Log can be installed through AWS CloudFormation. For more information about AWS CloudFormation, see the following link.
Checking the roles
To install WhaTap's AWS RDS Log via AWS CloudFormation, first check the required IAM roles.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"cloudformation:CreateStack",
"cloudformation:UpdateStack",
"cloudformation:DeleteStack",
"cloudformation:DescribeStacks",
"cloudformation:DescribeStackEvents",
"cloudformation:DescribeStackResource"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"s3:CreateBucket",
"s3:PutBucketVersioning",
"s3:PutBucketPublicAccessBlock"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"lambda:CreateFunction",
"lambda:UpdateFunctionCode",
"lambda:UpdateFunctionConfiguration",
"lambda:DeleteFunction",
"lambda:AddPermission"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"iam:CreateRole",
"iam:GetRole",
"iam:AttachRolePolicy"
],
"Resource": "*"
}
]
}
Installation and configuration
-
It can be installed using the AWS CloudFormation template provided by WhaTap. Access the following link and then enter the following items in the Parameters section.
AWS CloudFormation Install-
Host: Address of the WhaTap collection server. It can be viewed in Management > Agent Installation under the WhaTap project. e.g. 13.124.11.223 / 13.209.172.35
-
MemorySize: WhaTapRDSLog's memory size. Enter a value between 128 MB and 10,240 MB.
-
Pcode: Project code of a WhaTap project. Check the pcode in Management > Project Management.
-
ProjectAccessKey: Access key of a WhaTap project. Check the Project access key in Management > Project Management.
-
TimeOut: Maximum time in which the installed WhatTapRDSLog is maintained while running.
-
UseReservedConcurrency: Whether or not to use the reserved concurrency for WhatTapRDS.
-
ReservedConcurrency: Maximum number of instances that WhatapRDS can run at the same time when using the reserved concurrency.
-
-
Access the following link for log monitoring configuration details.
AWS CloudFormation Setting -
In the Parameters section, enter the following:
-
AwsRdsNames: List of names of RDS clusters and instances to receive events
-
e.g. database-1, seoul-pro-db-01, seoul-pro-db-01-writer …
-
Enter
noneif you do not want to create an event rule.
-
-
RdsLogGroupName (1-9): RDS CloudWatchLogGroup name from which you want to receive logs
-
e.g. /aws/rds/seoul-pro-db-01
-
Enter
noneif you do not want to create a subscription filter.
NoteYou can connect up to 9 CloudWatch log groups.
-
-
WhaTapRDSLogArn: WhataTapRDSLogArn generated in the previous step
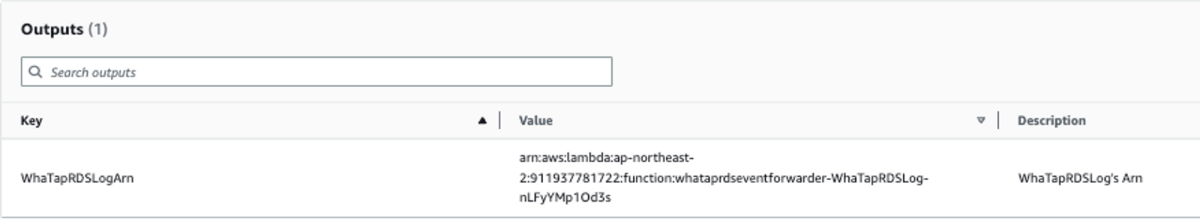
-
Checking the created resourced
Check the resources installed through AWS CloudFormation.
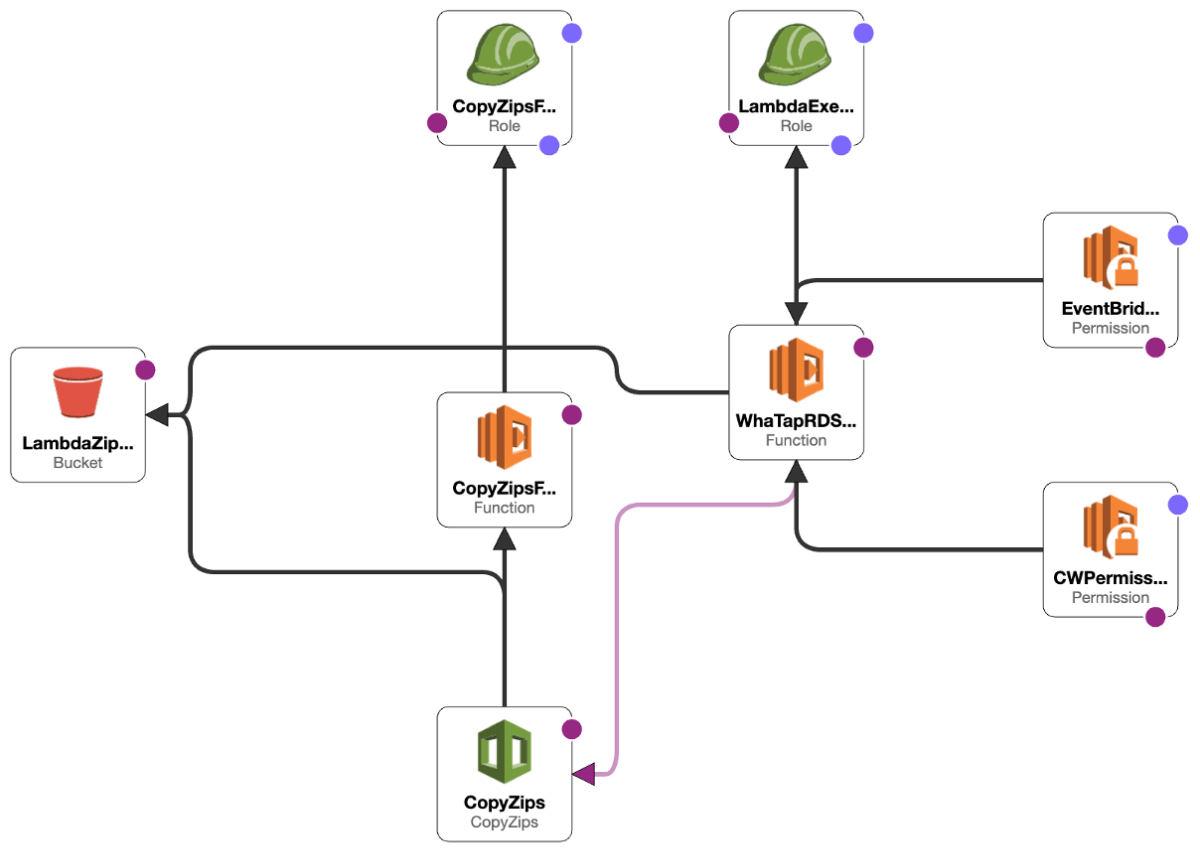
-
S3
- Bucket: AWS S3 bucket (CopyZips) that stores executable files of WhaTap AWS RDS Log
-
Lambda
-
Function
-
CopyZipsFunction: AWS Lambda function that moves executable files from the WhaTap AWS S3 bucket to your environment
-
WhaTapRDSLog: AWS Lambda function for AWS RDS monitoring
-
-
Permission
-
CWPermission: Permission to run WhataTapRDSLog when logs are created in RDS CloudWatchLogGroup
-
EventBridgePermission: Permission to run WhataTapRDSLog in EventBridge when RDS events occur
-
-
Role
-
Role required for CopyZipsFunction to get files from WhaTap's S3 and put them into CopyZips
-
Role required for WhatTapRDSLog to leave logs in CloudWatchLogGroup
-
-
Checking the filters and rules
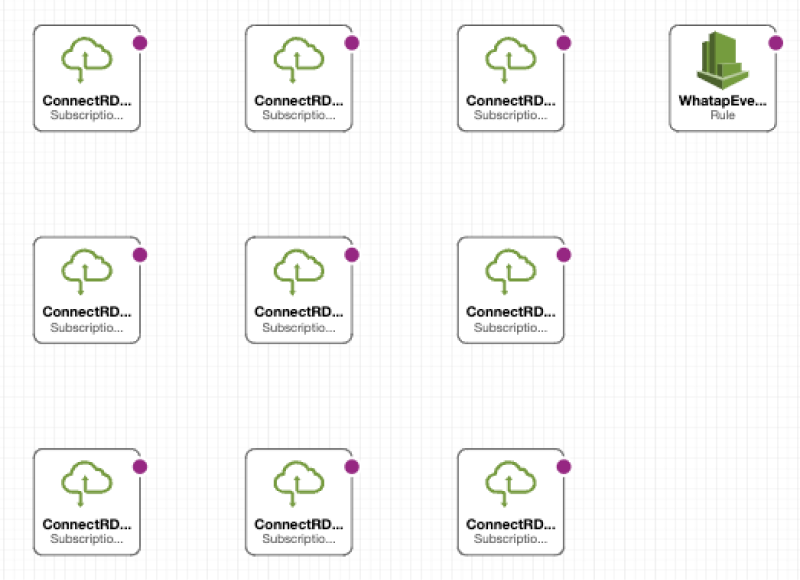
-
WS CloudWatchLogGroup
SubscriptionFilter (1-9): Filter that executes WhatapRDSLog when logs come into the CloudWatch LogGroup of RDS.
-
AWS EventBridge
Rule: Rule that triggers WhatapRDSLog when RDS events occur among AWS events
Starting the log monitoring
After configuring all settings, go to Log > Log Configuration to activate the log monitoring.