Options for collection of AWS resource data
To use the network performance monitoring in the AWS environment, you can collect data on the EC2 network interface (ENI) connected to each resource (e.g. LB) and then represent it in the topology. Because the agent cannot be installed directly as an AWS element, the associated ENI is displayed after checking based on the collected IP.
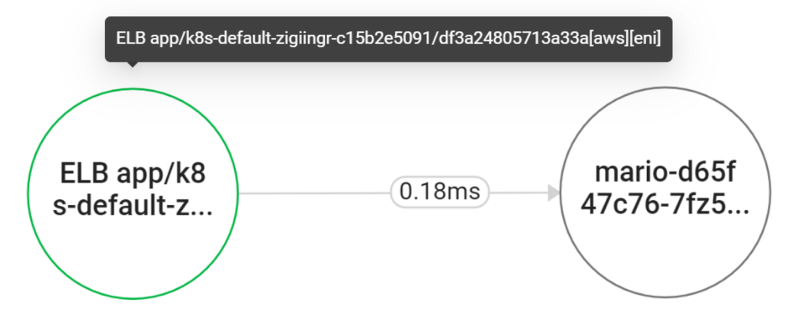
When traffic is applied internally through AWS's ELB, it can appear in the topology through the data displayed in ENI, as shown in the figure. It appears based on the Description field in AWS's ENI. If you do not leave any data in the Description field, the NetworkInterfaceId property is provided.
Configuring the AWS resource roles in the EC2 environment
When you install the NPM agent on AWS EC2, you can collect resource data from AWS based on the IAM settings.
Configuring the AWS IAM
AWS IAM requires you to specify minimum roles during policy configuration. To collect the AWS resource data from NPM, the ec2:DescribeNetworkInterfaces role is required.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
//...
"ec2:DescribeNetworkInterfaces"
],
"Resource": "*"
}
]
}
For more information about the policy and authorization, see the following link.
Configuring the AWS resource roles in the EKS environment
While installing the NPM agent on AWS EKS, you can collect resource data from AWS through SeviceAccount.
Configuring the AWS IAM
AWS IAM requires you to specify minimum roles during policy configuration. To collect the AWS resource data from NPM, the ec2:DescribeNetworkInterfaces role is required.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
//...
"ec2:DescribeNetworkInterfaces"
],
"Resource": "*"
}
]
}
For more information about the policy and authorization, see the following link.
Configuring the service account
During the AWS EKS configuration, connect IAM to the Kubernetes service account. To collect AWS resource data from NPM, connect IAM to the NPM service account.
For NPM, use the following service account.
namespace : whatap-npm-ns
service_account : whatap-npm
kubectl annotate serviceaccount -n whatap-npm-ns whatap-npm eks.amazonaws.com/role-arn=arn:aws:iam::$account_id:role/$role