AJAX hitmap pattern
Home > Select Project > Alert > Event Configuration > AJAX hitmap pattern
It automatically recognizes AJAX distribution patterns through machine learning and sends alert notifications. You can quickly and accurately recognize issue situations without setting complex conditions. Numerous hitmap patterns have been learned, so you can receive an alert when any similar pattern is detected in the data collected in real time.
-
This menu can also be accessed via the following menu path: Home > Select Project >
Sitemap > Alert > Event Configuration
New -
For more information about the Event Configuration
Newmenu, see the following. -
For more information about the AJAX Hitmap menu, see the following.
Basic options
You can set the method how to receive notifications through the following options:
-
Detection exclusion time: Patterns out of the set time are ignored.
-
Silent: This option can prevent excessive alerts from happening. No alerts are sent for the selected period after the first alert notification is generated. In addition, they are not recorded in Event History.
-
Event reception tag: You can send alerts to specific members or teams. If the tag is not set, notifications are sent to all members. For more information about the tag settings, see the following.
-
Save: The settings are saved and applied.
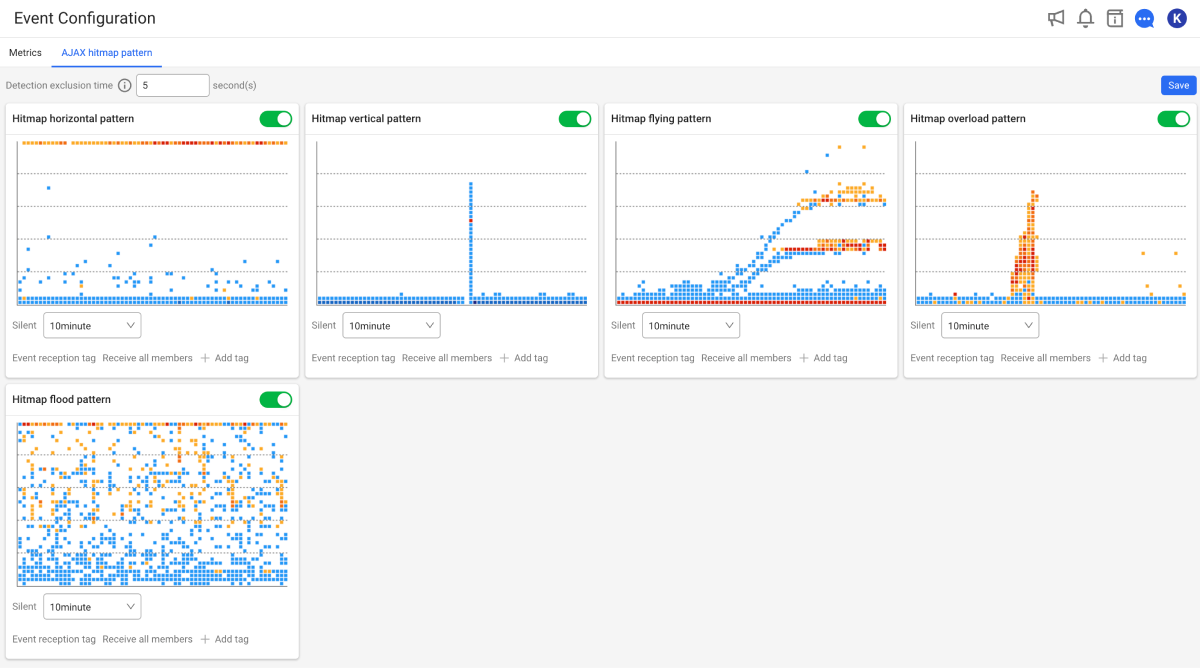
Hitmap patterns
You can set the alerts to be sent when any of the following hitmap patterns occur. This alert can be enabled or disabled by selecting the toggle buttons for each item.
In this pattern, requests are concentrated and terminated when specific response times are delayed. This occurs when requests are accumulated or response delays by specific APIs persist.
In this state, requests are concentrated at a specific time point, resulting in different response times. This can happen when a specific event causes a temporary load or processing of multiple types of API calls simultaneously.
This symptom means a gradual increase in response time. The main causes include the server memory leak, cache inefficiency, and connection pool exhaustion.
This pattern is characterized by requests being concentrated in a specific time section and having high response times. The main causes include the lack of server resources, database overload, and network bottlenecks.
In this pattern, the number of requests suddenly increases and the response time increases sharply at the same time. This phenomenon is typically caused by DDoS attacks, traffic surges triggered by specific events, or abnormal API calls.