Okta integration
You can integrate WhaTap Monitoring with Okta, a cloud-based solution for managing user accounts and access permissions. The Okta solution allows you to log on to numerous applications with a single account in high-level security environments. You can log on to the WhaTap services with the Okta account in your organization and use the services with the given roles.
-
To enable the log on to WhaTap, a user must have an Okta account.
-
For more information about Okta, see the following link.
Okta integration
Follow the instructions below to configure the Okta integration with the WhaTap monitoring service.
Issuing an SSO key from WhaTap
-
Log in the WhaTap monitoring service (https://service.whatap.io).
-
Select the profile icon on the upper right of the screen.
-
If a pop-up menu appears, select Manage Accounts.
-
In the menu on the right of the screen, select SSO Integrations.
-
Enter the key name in Issue SSO Key within the Service provider ID (WhaTap) section.
The key name can be entered by the user.
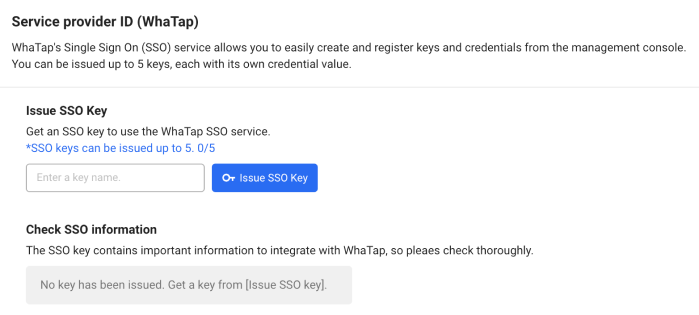
-
Select Issue SSO Key.
-
In Check SSO information, check the values for EntityID and Sign-On URL and then copy them.
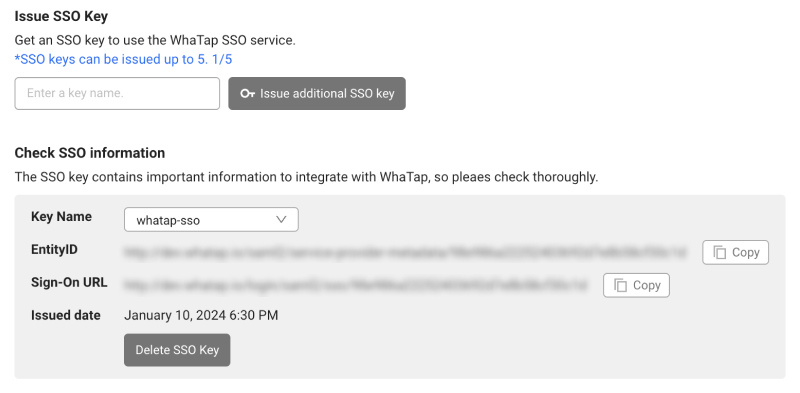
-
Up to 5 SSO keys can be issued, and each has its own unique authentication data.
-
Select Issue additional SSO key, add the SSO key, and then proceed with the next procedure.
-
For the added SSO information, select and check the list box in Key Name.
Configuring the Okta authentication
-
Access the Okta Admin page.
-
Go to Applcations > Applications.
-
Select Create App Integration.
-
If the Create a new app integration pop-up window appears, click SAML 2.0 and then select Next.
-
Enter the value for App name and then select Next.
-
Enter the General items in the SAML Settings section sequentially.
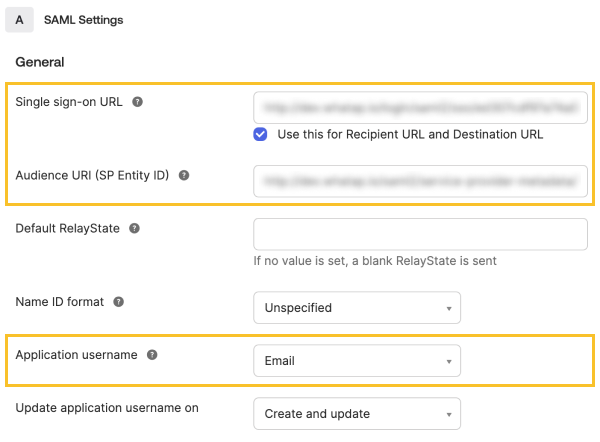
-
Single sign-on URL: Enter the Sign-On URL among the SSO-related data issued from WhaTap.
-
Audience URI (SP Entity ID): Enter the value for EntityID from the SSO data issued from WhaTap.
-
In the Application username list, select Email.
-
-
In Attribute Statements (optional), enter
emailin Name and then select user.email in Value.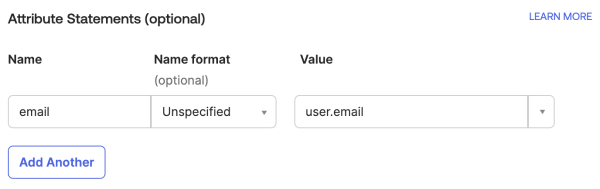
-
Select Next.
-
On the next screen, select This is an internal app that we have created and then select Finish.
Copying the Okta meta data
-
Access the Okta Admin page.
-
Go to Applcations > Applications.
-
Select the Sign On tab.
-
In Metadata URL, select Copy.
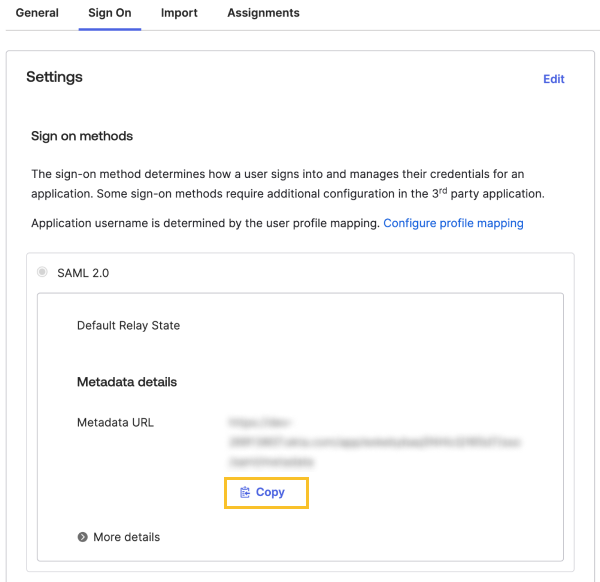
-
To register the copied value, go to the WhaTap's SSO Integrations menu.
Registering the external Idp in WhaTap
-
In the WhaTap monitoring service, go to SSO Integrations.
-
In the Credentials section, select Register External IdP.
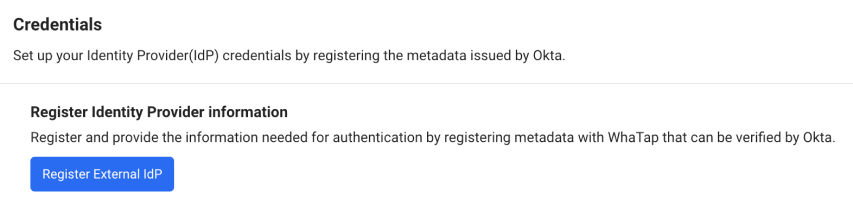
-
If the Register External IdP window appears, paste the Metadata URL copied from Okta to Metadata.
-
Select Register Metadata to automatically convert the authentication data.
-
Select Save.
The SSO linking is now finished.
Assigning users
-
Access the Okta Admin page.
-
Go to Applcations > Applications.
-
Select the application added from the list.
-
Select the Assignments tab.
-
Click Assign and then select Assign to People (or Assign to Groups).
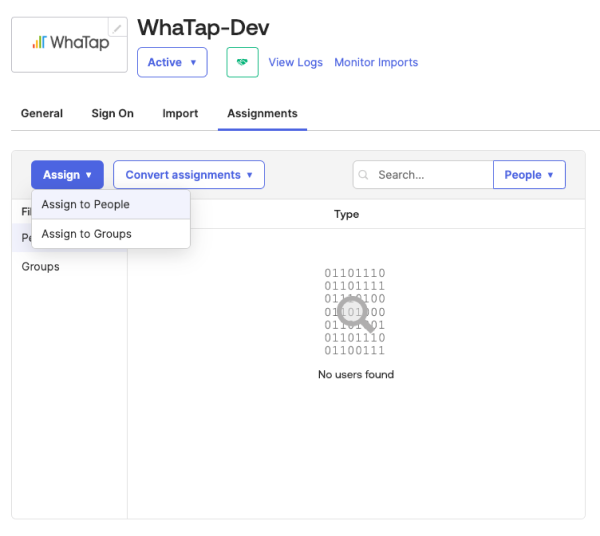
-
Assign desired users.
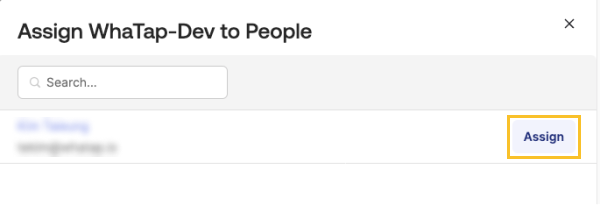
-
Select Save and Go Back.
-
Finish all the steps and then select Done.
Checking the SSO linking
-
Access the Okta Admin page.
-
Go to Applcations > Applications.
-
Select the application added from the list.
-
Select the General tab.
-
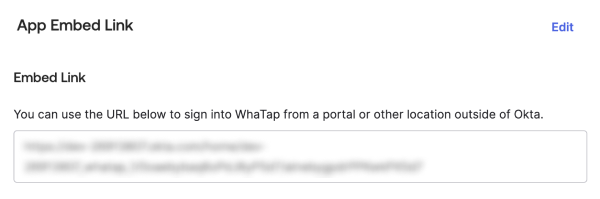
Scroll down to App Embed Link.
-
Copy the URL in Embed Link.
-
Go to the copied URL in your web browser.
If you can log on to the WhaTap monitoring service, the connection is successful.
-
If SSO has been linked for the first time, it is required to register the link information (automatic) through password authentication when the email account exists in WhaTap.
-
If you have no email address, registration of WhaTap membership and link information is automatically performed after entry of the required data.
Deleting the SSO key
-
In the WhaTap monitoring service, go to SSO Integrations.
-
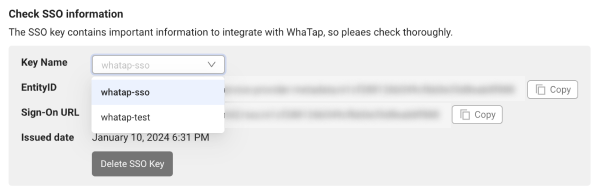
In the Service provider ID (WhaTap) section, select the Key Name to delete from Check SSO information.
-
Select Delete SSO Key.
-
If the deletion confirmation window appears, select Delete SSO Key.
Modifying/deleting an external IdP
-
In the WhaTap monitoring service, go to SSO Integrations.
-
In the Credentials section, select Modify External IdP.
-
If the Modify External IdP window appears, paste the Okta meta data to Meatadata.
-
Select Register Metadata to automatically convert the authentication data.
-
Select Save.
To delete the External IdP information, click Modify External IdP and then select Delete in the pop-up window.