Microsoft Entra ID linking
The following explains how to link the WhaTap monitoring service account based on the Microsoft Entra ID. You can log in to the WhaTap monitoring service with the Microsoft Entra ID account and use the WhaTap monitoring service within the assigned roles.
Here are the steps to link the Microsoft Entra ID account with the WhaTap monitoring service.
- Checking accounts (email) to use
- Generating the link (SSO) key from WhaTap
- Creating a Microsoft Entra ID Enterprise Application
- Allocating users to the application
- Configuring the Microsoft Entra ID authentication
- Registering the metadata in WhaTap
- Link testing
- Managing WhaTap accounts in the Enterprise Application
For more information about Microsoft Entra ID, see the following link.
Checking accounts (email) to use
Before you begin, make sure you have an account with WhaTap and Microsoft Entra services.
In case an account has been created with WhaTap
If you already have an account created in WhaTap to use with the Microsoft Entra ID, see the following.
-
For linking, the names of the accounts used in each service must be the same, as in the following example.
-
WhaTap: monitoring1@abc.com
-
Microsoft Entra: monitoring1@abc.com
-
-
If the account names used for each service are different as in the following example, linking is not possible.
-
WhaTap: monitoring2@abc.com
-
Microsoft Entra: monitoring3@abc.com
-
In case there is no account with WhaTap
If the account you use for Microsoft Entra ID does not exist in WhaTap, it is required to authenticate yourself once to verify the identity.
-
Log on to My Apps portal with your company or school account. The My Apps page appears, displaying all organizations' cloud-based Apps that are available.
-
Access the WhaTap service through the enterprise application registered in Apps dashboard.
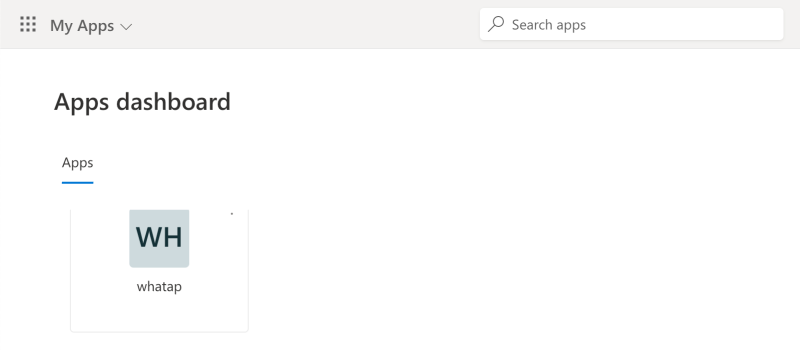
-
Enter your name and company on the accessed screen to link authentication.
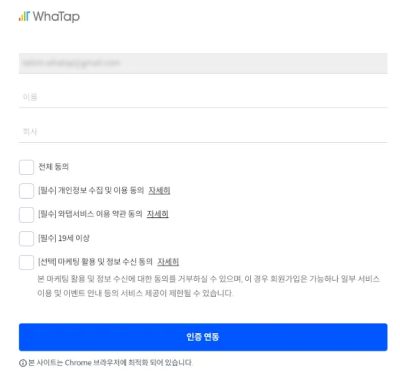
-
If the error page appears, close the page and then click the WhaTap application again in Apps dashboard for normal log in.
Generating the link (SSO) key from WhaTap
The following explains how to obtain an SSO key from the WhaTap Monitoring Service screen. You can link the Microsoft Entra ID with the received SSO key. If configuration for Microsoft Entra ID linking is made for the first time, you must create a WhaTap account. If there is no WhaTap account, see the following.
-
Log on to the WhaTap Monitoring service with the account to link with the Microsoft Entra ID.
-
Select the profile icon on the upper right of the screen.
-
If a pop-up menu appears, select Manage Accounts.
-
In the menu on the right of the screen, select SSO Integrations.
-
Enter the key name in Issue SSO Key within the Service provider ID (WhaTap) section.
The key name can be entered by the user.
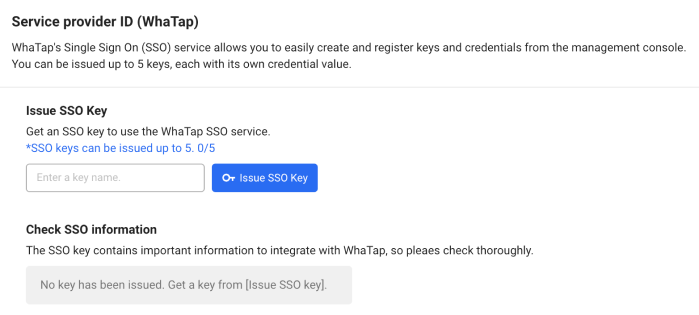
-
Select Issue SSO Key.
-
In Check SSO information, check the values for EntityID and Sign-On URL and then copy them.
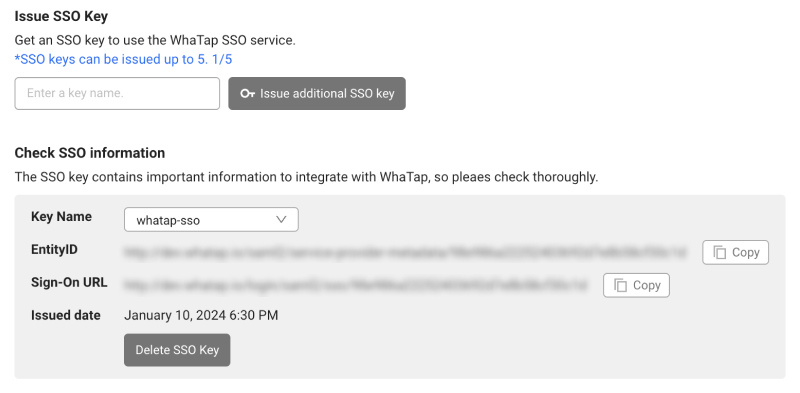
-
Up to 5 SSO keys can be issued, and each has its own unique authentication data.
-
Select Issue additional SSO key, add the SSO key, and then proceed with the next procedure.
-
For the added SSO information, select and check the list box in Key Name.
Creating a Microsoft Entra ID Enterprise Application
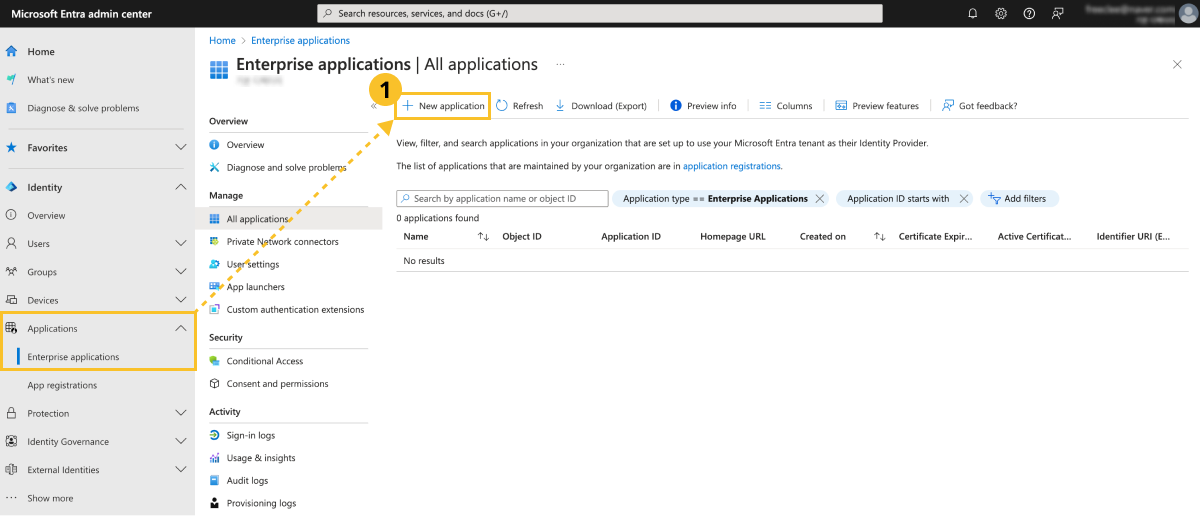
Go to the Microsoft Entra Admin Center service, log in, and create Enterprise applications by following steps:
-
In Identity > Applications > Enterprise applications, click New application.
-
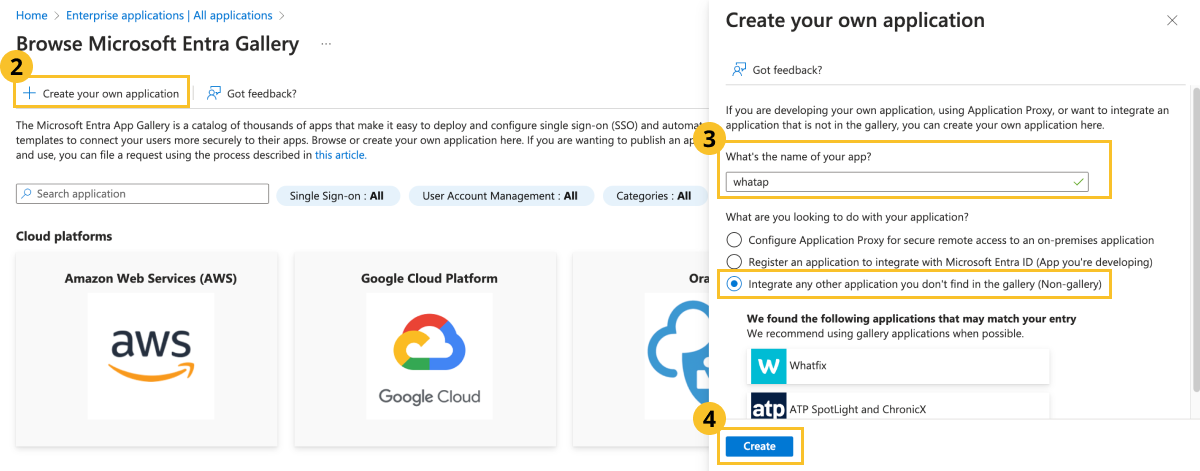
Click Create your own application.
-
If the App name configuration screen appears on the right, enter the App name and then click the Integrate any other application you don't find in the gallery (Non-gallery) option.
-
At the bottom of the screen, click Create.
Allocating users to the application
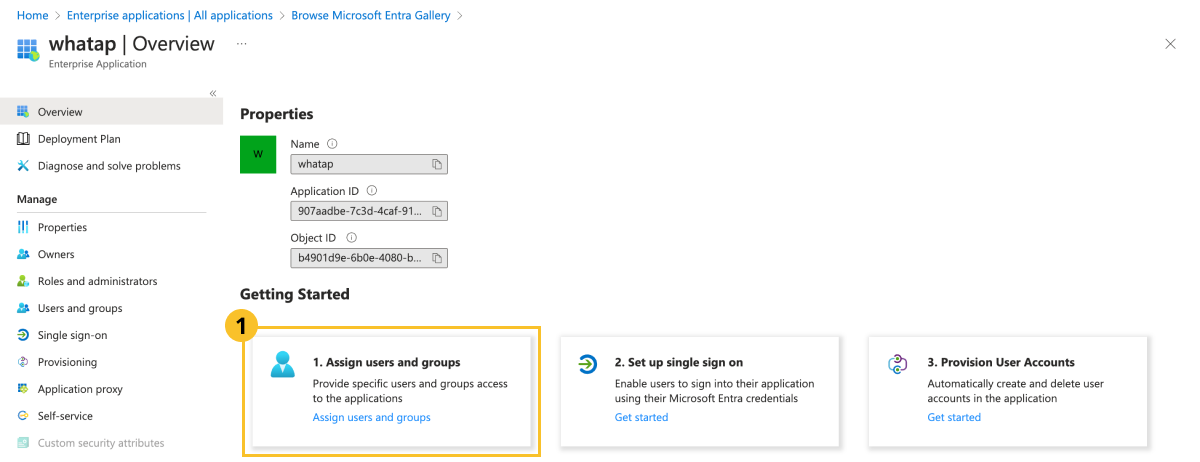
Assign the users to link to in the newly created Enterprise Application screen.
-
Click Assign users and groups.
-
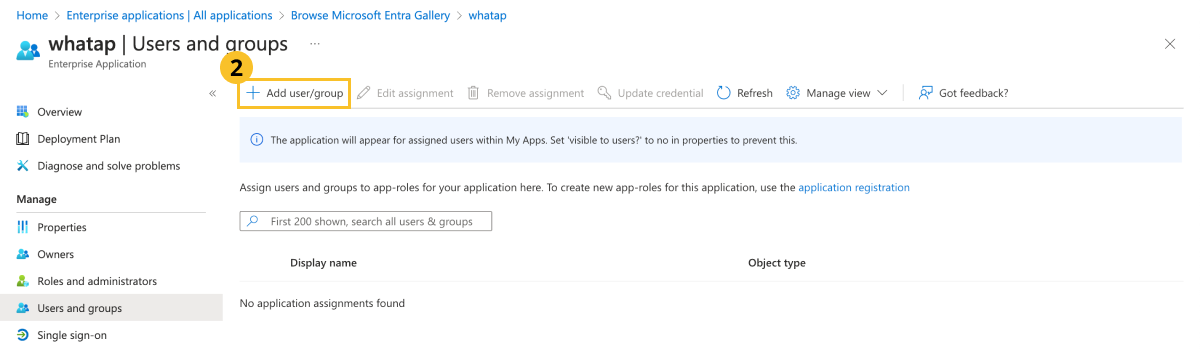
Click Add user/group.
-
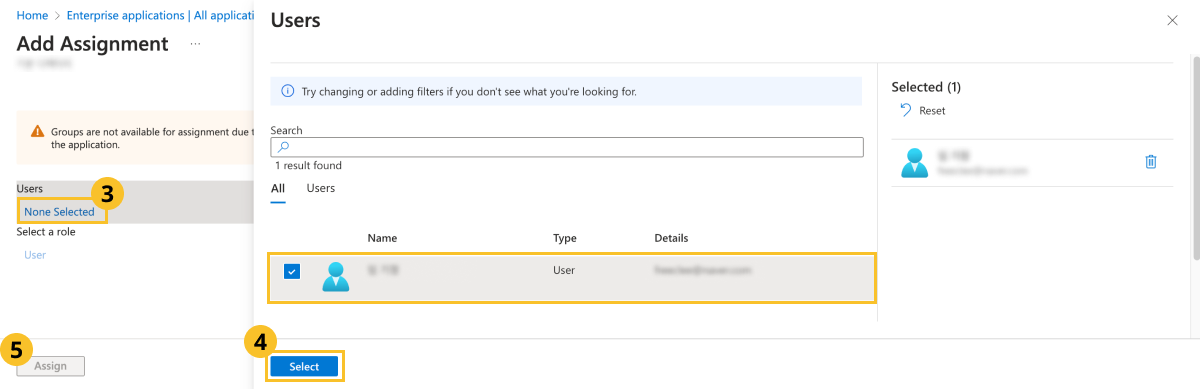
In Add Assignment, click None Selected.
-
Select users to link with in the user list and then click Select.
-
At the bottom of the screen, click Assign.
Configuring the Microsoft Entra ID authentication
Allow users to log on to the application by using the Microsoft Entra verification.
-
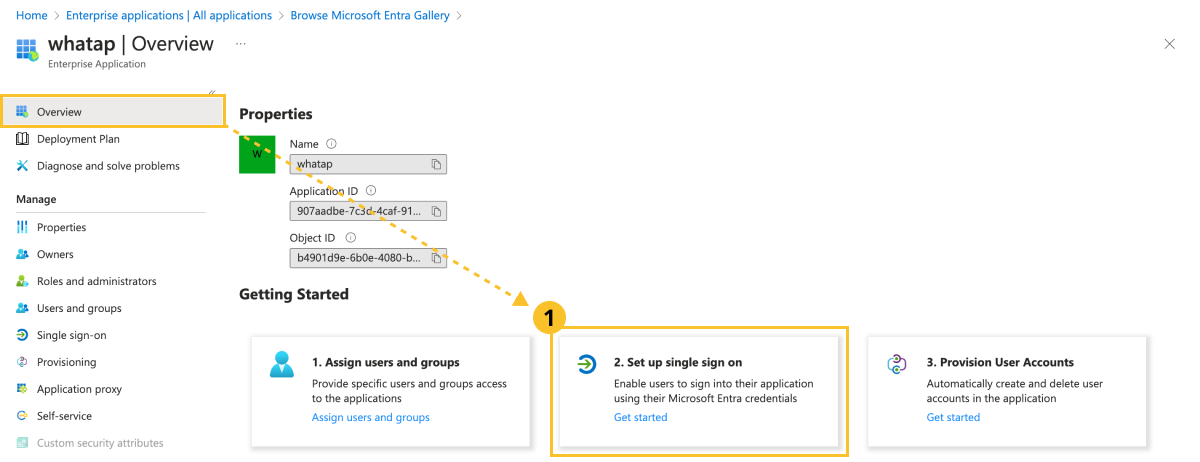
Select Overview for the enterprise application to go to the initial screen, and then click Set up single sign on.
-
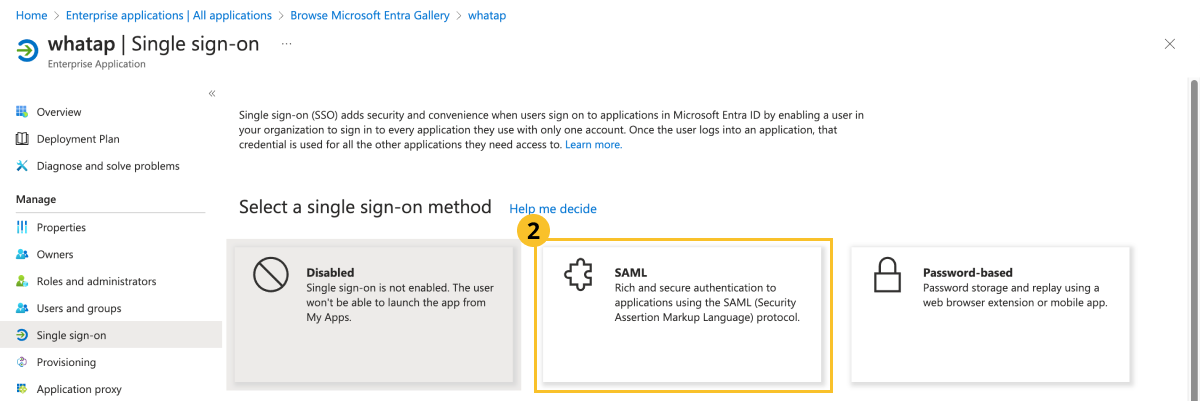
In Select a single sign-on method, click SAML.
-
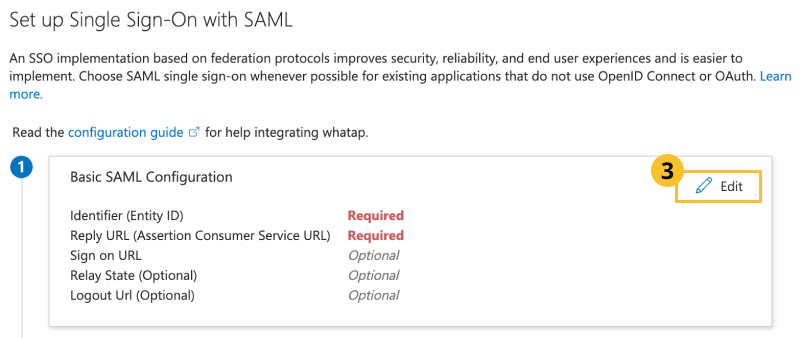
In Basic SAML Configuration, click Edit.
-
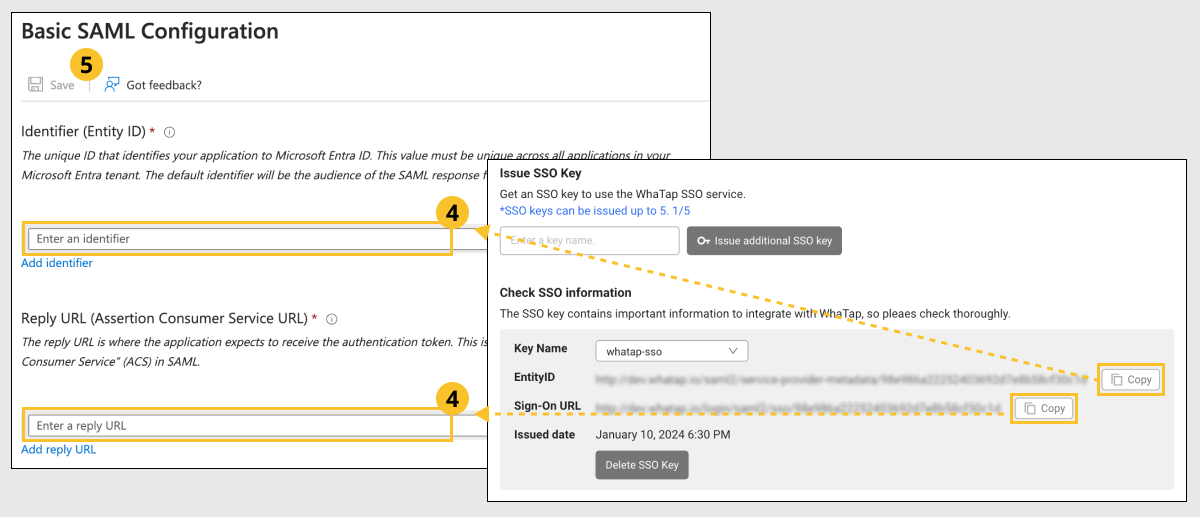
In the WhaTap SSO Integrations screen, enter the created SSO information.
-
Copy the value of EntityID, click Add identifier, and paste it into Enter an identifier.
-
Copy the value of Sign-On URL, click Add reply URL, and paste it into Enter a reply URL.
-
-
Click Save.
-
In Attributes & Claim, click Edit.
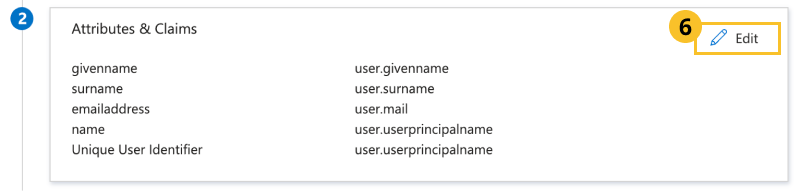
-
Click Unique User Identifier (Name ID).
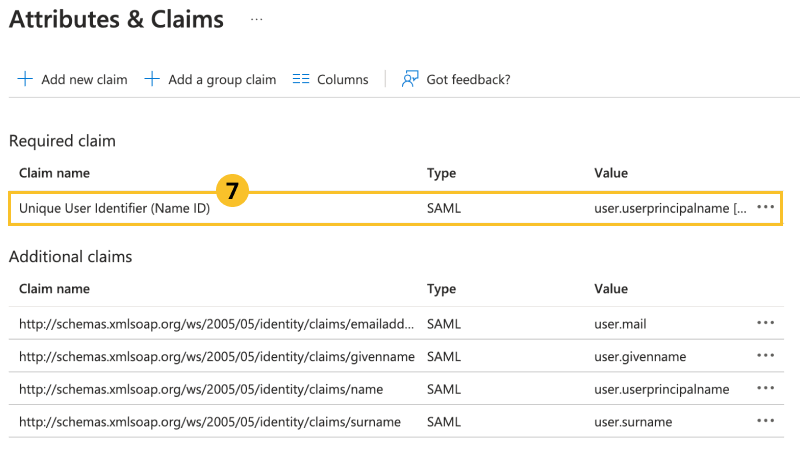
-
In Source attribute, select user.mail and then click Save.
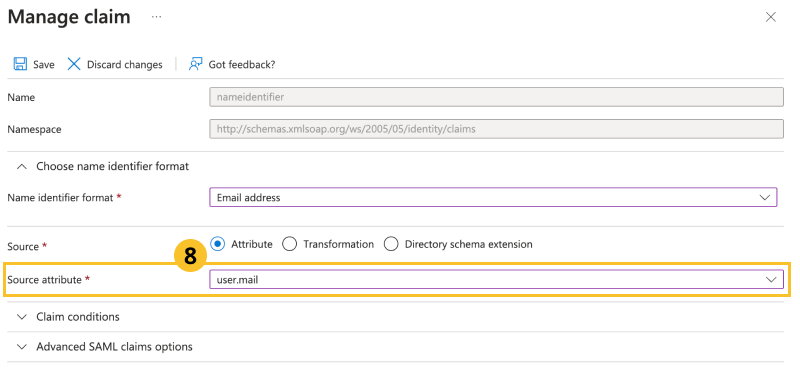
-
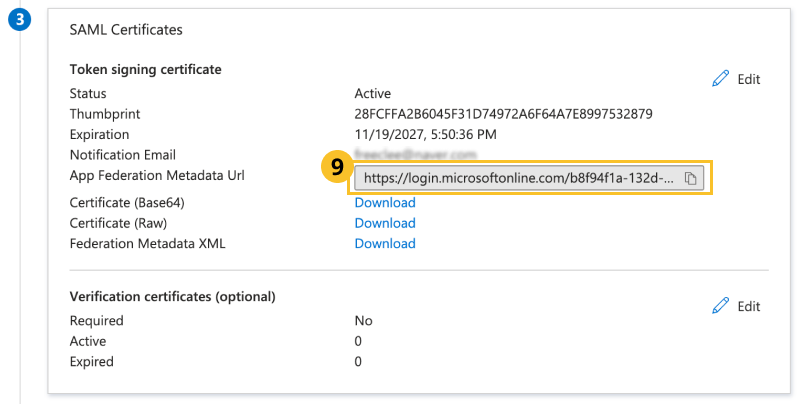
In SAML Certificates, copy the value inApp Federation Metadata Url.
Registering the metadata in WhaTap
Link the authentication information by registering the metadata issued by Microsoft Entra ID.
-
In the WhaTap monitoring service, go to SSO Integrations.
-
In the Credentials section, select Register External IdP.
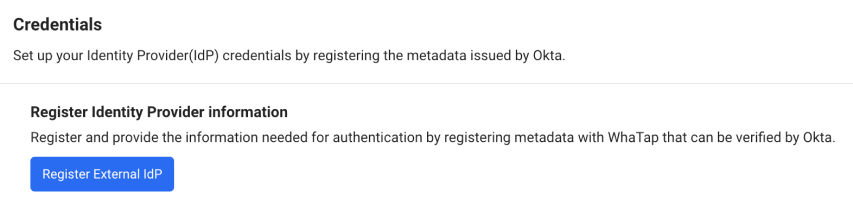
-
When the Register External IdP window appears, paste the metadata value copied from Microsoft Entra ID to Metadata.
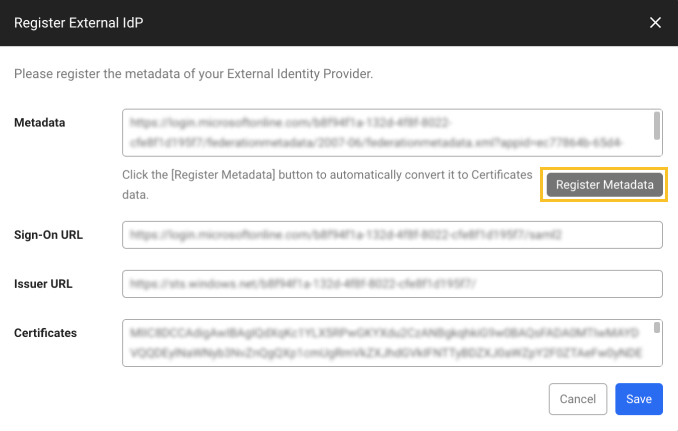
-
Select Register Metadata to automatically convert the authentication data.
-
Select Save.
Link testing
Return to the Microsoft Entra ID screen and then test the operation of Single Sign On.
-
In Test Single Sign-On, click Test.
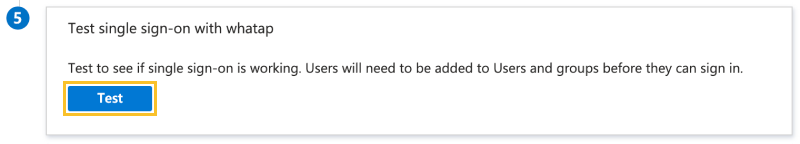
-
Click Test sign in.
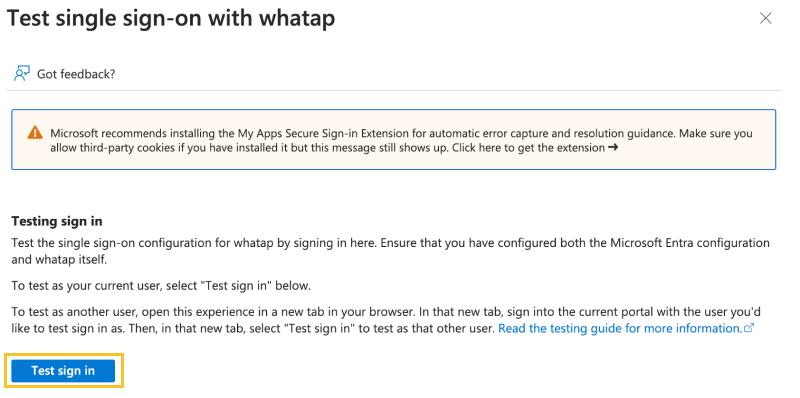
-
If you have a WhaTap account, the WhaTap Monitoring service screen appears.
-
If you do not have a WhaTap account, create a new account through the authentication.
Managing WhaTap accounts in the Enterprise Application
To manage WhaTap accounts in the enterprise applications with Microsoft Entra ID, go to the following link.
-
Information on My Account invited to the enterprise application
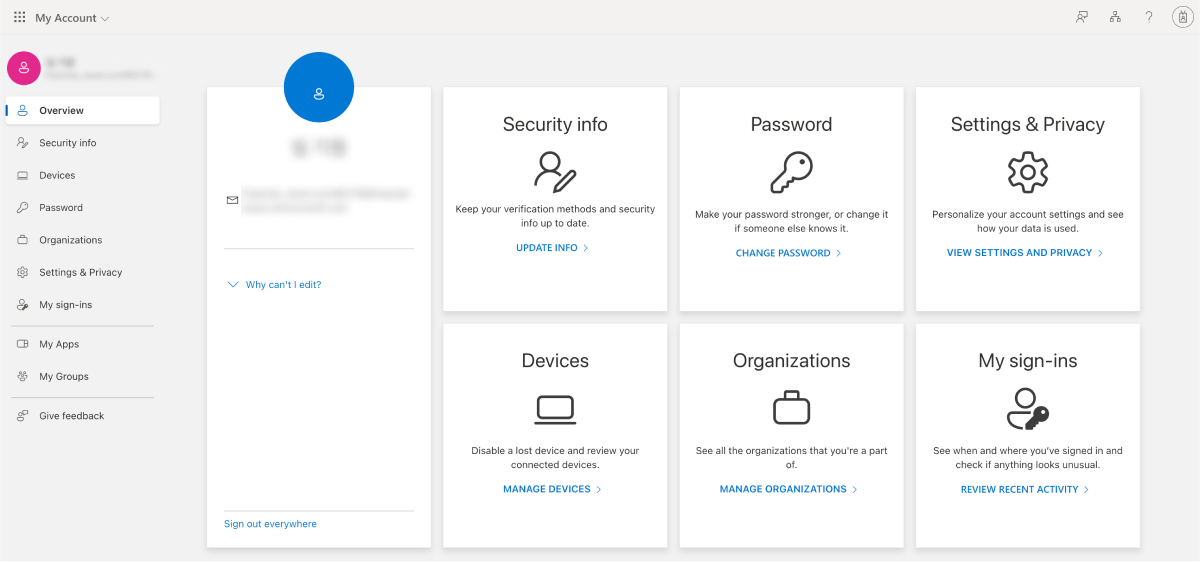
-
My Apps information of the invited account

Deleting the SSO key
-
In the WhaTap monitoring service, go to SSO Integrations.
-
In the Service provider ID (WhaTap) section, select the Key Name to delete from Check SSO information.
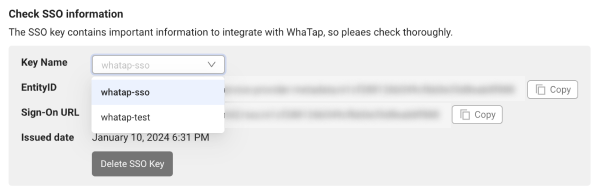
-
Select Delete SSO Key.
-
If the deletion confirmation window appears, select Delete SSO Key.
Modifying/deleting an external IdP
-
In the WhaTap monitoring service, go to SSO Integrations.
-
In the Credentials section, select Modify External IdP.
-
When the Register External IdP window appears, paste the metadata value copied from Microsoft Entra ID to Metadata.
-
Select Register Metadata to automatically convert the authentication data.
-
Select Save.
To delete the External IdP information, click Modify External IdP and then select Delete in the pop-up window.